Beyond the Scan: Manual Pentesting, Automated Testing, and Why Exposure Validation Is the Missing Link
Security practitioners today are overwhelmed with tools — vulnerability scanners, pentests, red teaming, EASM, and more — each promising to improve your security posture. But understanding what each one actually does, when to use it, and what gaps remain isn’t always clear.
In this post, we’ll break down three common approaches — manual pentesting, automated pentesting, and adversarial exposure validation (AEV) — to help you understand where each fits, what they’re best at, and why validation may be the most critical piece your security program is missing.
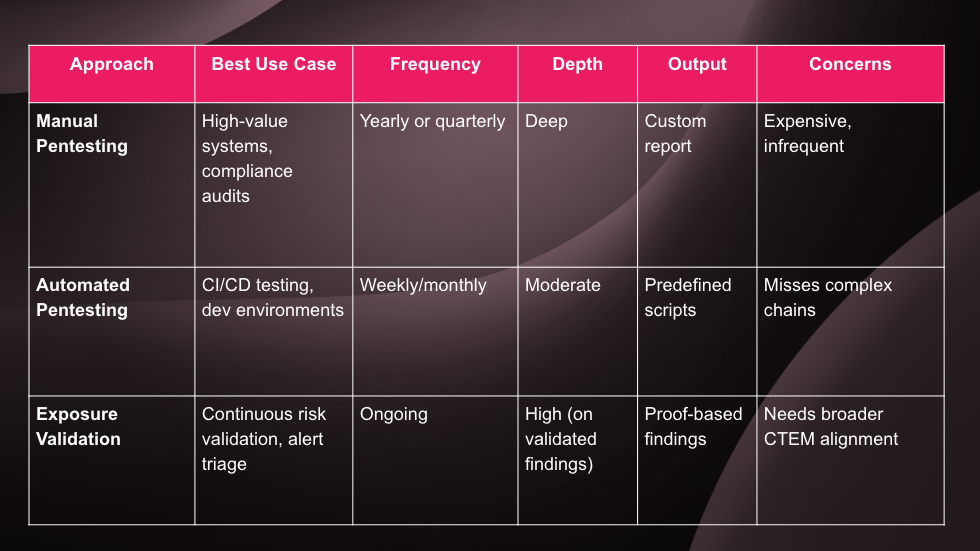
Manual Pentesting: Deep, But Infrequent
What it is:
Manual penetration testing simulates real-world attacks by hiring skilled security professionals to probe your environment. They use creativity, expertise, and up-to-date TTPs (tactics, techniques, and procedures) to uncover vulnerabilities and exploitation paths.
Pros:
- Mimics how actual attackers think and behave
- Can identify complex chained exploits and logic flaws
- Great for compliance checkboxes and high-value assessments (e.g., before going live)
Cons:
- Infrequent and expensive
- Not scalable
- Results go stale quickly in dynamic environments
- Focused on threat detection, not always on validation and remediation
Best for:
Critical systems, compliance requirements, and once-a-year security milestones.
Automated Pentesting: Fast, But Surface-Level
What it is:
Automated pentesting tools replicate some techniques of manual testing using predefined scripts and automation. Think of it as scalable, software-driven red teaming — often integrated into CI/CD pipelines or run on demand.
Pros:
- Faster and more affordable than manual testing
- Repeatable and scalable
- Integrates easily into dev and staging environments
Cons:
- Limited in sophistication — misses context and chained exploits
- Can generate false positives without validation
- Still focuses on discovery, not true risk
Best for:
Testing during development, staging environments, or augmenting manual tests between engagements.
Adversarial Exposure Validation: Real Risk, Real Proof
What it is:
Exposure validation flips the script. Instead of just discovering theoretical vulnerabilities, it validates what attackers can actually exploit in your environment right now — with real, safe proof of exploitability. This approach tests exposures in context: is this internet-facing system actually exploitable? Can this misconfiguration be leveraged for lateral movement?
Pros:
- Focuses on exploitable exposures, not just vulnerabilities
- Drastically reduces false positives and alert fatigue
- Provides clear, actionable proof to help teams prioritize and remediate
- Can run continuously, across your entire attack surface
Cons:
- Still an emerging category — many tools claim validation, few deliver it well
- Needs integration into broader CTEM strategy for full value
Best for:
Day-to-day risk management, prioritization of remediation efforts, breach readiness, and reducing noise from security tools.
Choosing the Right Approach: When to Use Each One
Each approach — manual pentesting, automated pentesting, and exposure validation — has its place in a mature security strategy. The key is knowing when to apply each one to get the most value.
Manual pentesting is best suited for deep-dive assessments where you want a skilled human to uncover sophisticated attack paths. If you’re preparing for a major compliance audit, launching a new product, or evaluating high-value systems, this approach brings human creativity and contextual understanding that tools alone can’t replicate. But because manual pentests are time-consuming and expensive, they’re not something you can rely on continuously. They give you a valuable snapshot — but snapshots don’t catch everything.
Automated pentesting offers a faster, more scalable alternative. It’s a solid choice when you want to maintain security hygiene in dev and staging environments or need frequent testing without the heavy costs of manual assessments. While automated tools are great for catching common misconfigurations or known exploits, they’re only as good as the scripts behind them — and they often miss the nuance of real-world exploitation. Use them to supplement, not replace, more contextual analysis.
Exposure validation, however, is where you shift from theory to reality. This approach doesn’t just ask “what might be vulnerable?” — it answers “what can actually be exploited right now in your environment?” Exposure validation brings clarity to the flood of alerts from scanners and pentests by focusing your attention on what attackers could realistically act on. It’s ideal for day-to-day operations, breach prevention, and executive reporting, because it delivers something the others don’t: proof.
If you’re overwhelmed with alerts or struggling to prioritize patching, exposure validation helps you gain clarity. It complements both manual and automated pentesting by helping your team validate findings, confirm risk, and act with confidence.
In short:
- Use manual pentesting for depth and creativity when it matters most.
- Use automated pentesting for breadth and speed during development and testing.
- Use exposure validation to stay grounded in reality, every day.
Together, these approaches can give you a balanced, layered defense. But if you’re missing validation, you’re likely fixing issues that don’t matter — and missing the ones that do.
Why Validation is the Way Forward
Security teams don’t need more alerts — they need more certainty. In a world where breach windows are short, attackers move fast, and resources are limited, validating what’s actually exploitable is no longer optional — it’s essential.
Exposure validation is what helps you:
- Eliminate scanner noise and false positives
- Show stakeholders real risk with real proof
- Prioritize exposures before attackers do
- Make better remediation decisions, faster
ULTRA RED: Built for Exposure Validation
ULTRA RED’s Continuous Threat Exposure Management platform combines attack surface discovery with real-world exposure validation. We help security teams focus on what truly matters — with proof, not guesswork.
Want to stop chasing ghosts and start fixing real issues?





